Oct 21, 2025
Imagine a city where every drop of water is accounted for, every pump is optimized, and every utility manager sleeps soundly knowing their digital infrastructure is resilient. This isn’t science fiction—it’s the promise of digital transformation in the water sector. But as we embrace smart sensors, cloud analytics, and remote operations, one question rises to the top: How do we protect the value these technologies deliver?
At Xylem, product security isn’t just a technical requirement—it’s a commitment to safeguarding the innovations that help communities thrive.
Why Product Security Matters—Beyond the Headlines
Water utilities face aging infrastructure, rising costs, and increasing demands for efficiency. Digital technology is a lever that helps solve these challenges, unlocking new capabilities for monitoring, control, and optimization. But the true value of digital transformation is only realized when customers trust that their systems are secure, resilient, and ready for tomorrow’s challenges.
Product security is how we ensure the value of digital technology. It’s not about fear—it’s about enabling progress.
Security as a Journey, Not a Destination
At Xylem, we see product security as an ongoing journey. Like maintaining a water pump or calibrating a sensor, security requires regular attention and improvement.
- An Ongoing Journey:
“If you rest, you rust.” Every year, our systems must be better than last year. We continuously reevaluate, test, and update our products to stay ahead of evolving threats and ensure lasting value. - Defense in Depth:
“None of us is as smart as all of us.” No single protection is enough. We build layers of security—redundancy, alerts, controls—so that even if one layer is bypassed, others stand ready. - A Shared Process:
“Teamwork makes the dream work.” Security is a community effort. Utilities, vendors, integrators, and service providers all share responsibility. We foster partnerships and transparency to build trust.
How We Deliver Product Security at Xylem
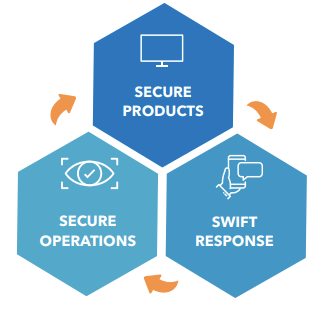
Our approach centers on three pillars:
1. Secure Products—Built from the Ground Up
We design products to be secure by default. Every new solution goes through a rigorous secure development framework, mapping data flows, identifying potential threats, and embedding security features from the start.
The journey of a product begins with a threat model – in which product security works with the product team to map out data flows and to consider ways to spoof, tamper, shut off those data flows. This exercise results in security requirements that are tracked through design and development. Throughout development, the code is tested automatically to look for thousands of typical security weaknesses, which are fixed before final testing. Finally, before release, security engineers try to manually exploit any weaknesses.
We follow global standards like ISA/IEC 62443-4-1, supplementing with best practices from OWASP and NIST. Our commitment is recognized: Xylem was one of the original signers of the Secure By Design Pledge (Secure by Design Pledge | CISA), helping set the bar for secure development in industrial automation and water technology.
2. Swift Response—Ready When It Counts
Security doesn’t end at launch. Our Product Security Incident Response Team (PSIRT) monitors research, reports, and incidents 24/7. If a threat emerges, we coordinate across teams to deliver guidance or patches—fast. (If you ever suspect something with our product, send a note to our PSIRT by emailing security@xylem.com.)
I remember once a construction project cut the primary fiber line at one of our data centers. Before customers noticed our PSIRT was in action coordinating the response across teams of experts and saw the issue resolved. Each report of a suspected product weakness considered a gift to help us continuously improve our security.
We partner with leading organizations like Dragos, WaterISAC, and FIRST.org to stay ahead of threats and continuously improve our response capabilities.
3. Secure Operations—Continuous Vigilance
For Xylem-hosted products, our Product Security Operations Center (PSOC) in Boise, ID, and our partners at Cyderes, monitor systems around the clock. We analyze logs, track indicators of compromise, and collaborate with the Joint Cyber Defense Collaborative (JCDC) to share intelligence and stop adversaries before they impact critical infrastructure.
The Bottom Line: Security Enables Progress
Governments and utilities are raising the bar for cybersecurity, with new regulations and standards. At Xylem, we don’t just meet these requirements—we help shape them. By partnering with global alliances and investing in secure development, rapid response, and continuous operations, we ensure that digital transformation delivers lasting value.
Product security isn’t about avoiding risk—it’s about unlocking opportunity. When utilities trust their technology, they can focus on what matters: delivering safe, reliable water to their communities.
The Water Tower consists of two nonprofit organizations: The Water Tower at Gwinnett, a 501(c)4 – responsible for the development and operations of the campus, and The Water Tower Institute, a 501c3 – responsible for solutions, instruction, and engagement programming. Together, these entities are cultivating an ecosystem of water innovation fueled by imagination, informed by research, and powered by pioneers. The Water Tower brings together public and private sectors of the water industry, side by side with academia and nonprofits, to tackle the industry’s greatest challenges.
